TOZED ZLT M30s Information Disclosure via Debug Interface
TOZED ZLT M30S v1.47 - Information Exposure via Debug Interface
9th Nov 2025
ZLT M30S v1.47 - Information Exposure via Debug Interface
Category: CVE
Researcher: Ramon Bello (gr33pp / S33K3R)
CVE-2025-15083
TL; DR
Information exposure vulnerability has been identified in TOZED ZLT M30S firmware verson v1.47. The device's internal Universal Asynchronous Reciever-Transmitter (UART) debugging console, logs the current and factory-set default Wi-Fi credentials in plain text during the boot and factory reset sequences, respectively.
POC
Access requirements: Requires Physical Access to the device, a USB-to-TTL serial adapter and some soldering skills :) (I have a bad soldering iron btw )
Steps
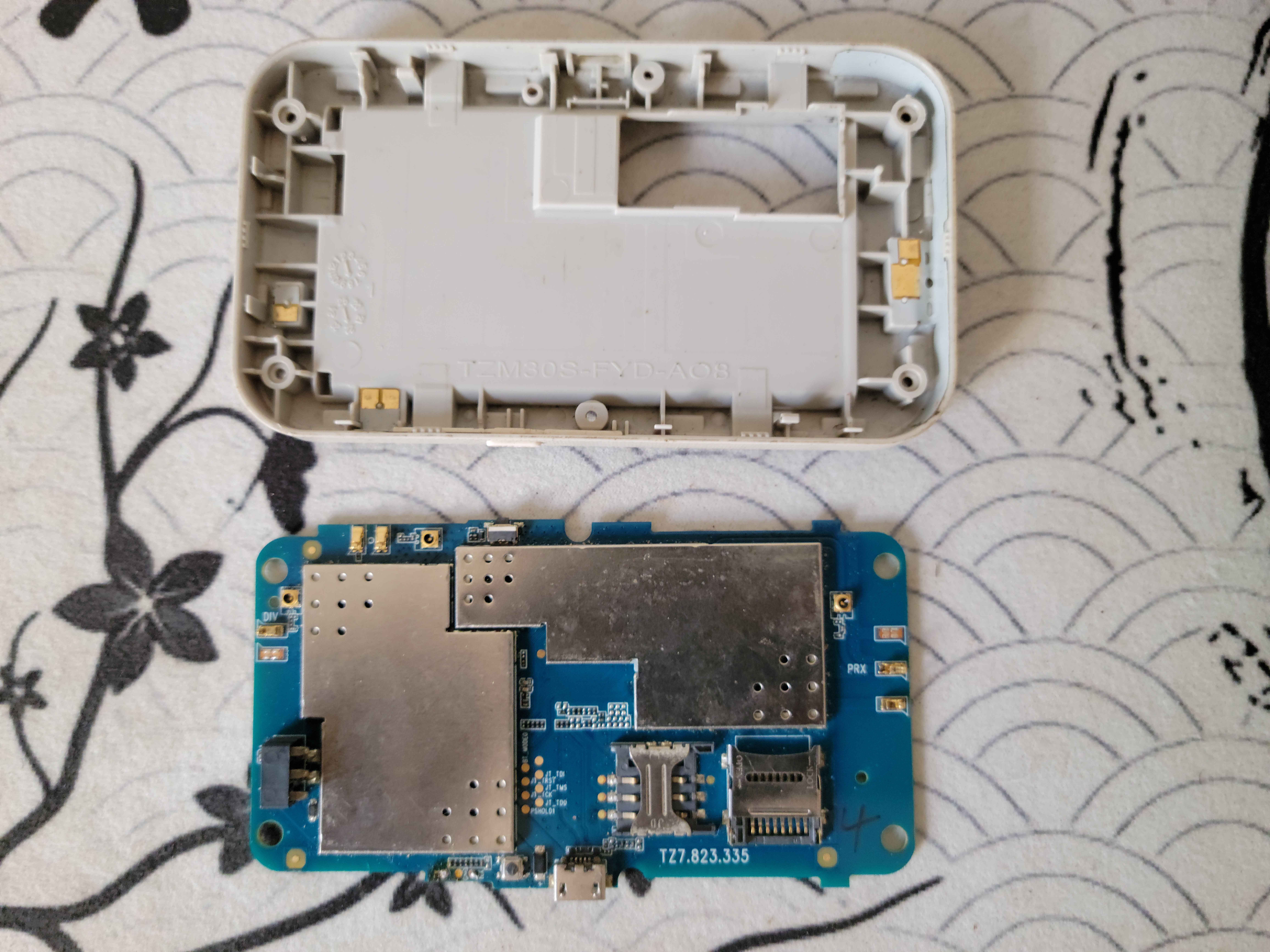
- Decouple the the mobile router and separate the PCB from the casing.

- Locate the UART pads, it is beside the reset button.
 TX GND RX pads identified
TX GND RX pads identified
- Using your soldering skills, attach wires to the three pads. GND pad is quite flexible, I took mine from the negative battery terminal (Remember I have a bad soldering iron TT )

- Connect the wires to your USB-to-TTL serial adapter. Here, I used a raspberry pico lying around as my serial adapter.

- Using a serial monitor, e.g picocom, minicom. Connect the serial adapter USB to a computer, identify the adapter
ttyname. Mine runs at/dev/ttyACM0. Launch picocom to use your serial adapter and the baud rate set to921600. I had to bruteforce to get the working baud rate. - If your router is turned on already, reboot it through the button and observe the serial monitor output, search for
inputStroroutputStr, there you will find the current Wi-Fi password set to the router.
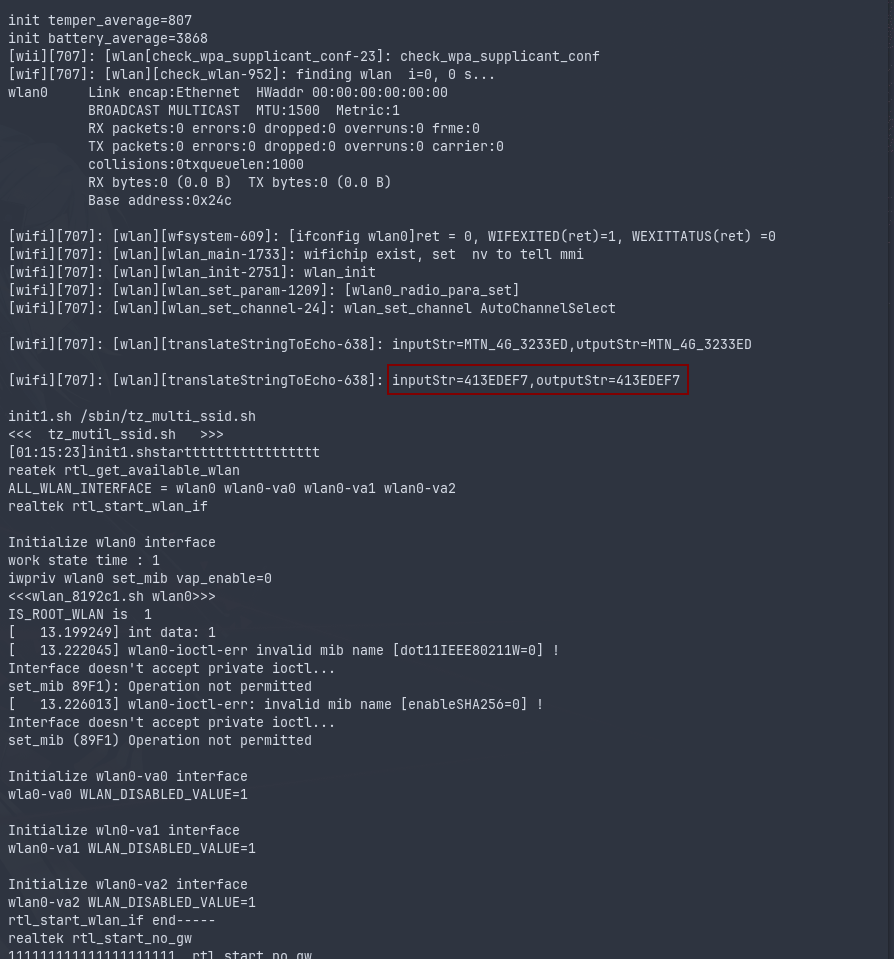
The same thing occurs on factory reset through the reset button, the logs reveals the default password to the router.

What next?

I still need proper hardware pentest tools. I'm open to sponsorships. My contact links are in the homepage and footer. Thanks for reading! :)